In order to ensure the images we create are tamper-proof (can not be switched/replaced or modified), we use digital signatures using GPG (https://www.gnupg.org/).
DFIR VN runs a double signature system for forensic captures.
- Once the image has been completed and has been verified with file format checks, an initial signature is created on the forensic imaging kit using the unique private key to that individual device.
- The removable drive is then detached from the forensic kit and attached to the specialist laptop, where it is verified a second time and then signed again with the unique private key for that DFIR employee.
The public keys used are available to all our customers in order to verify the signatures and image integrity at any time using open source tools. Kit specific keys are pass-phrase protected and not stored anywhere else. If we deemed them to be compromised, a revocation will be published stating that the key will be invalid for signatures after a particular date.
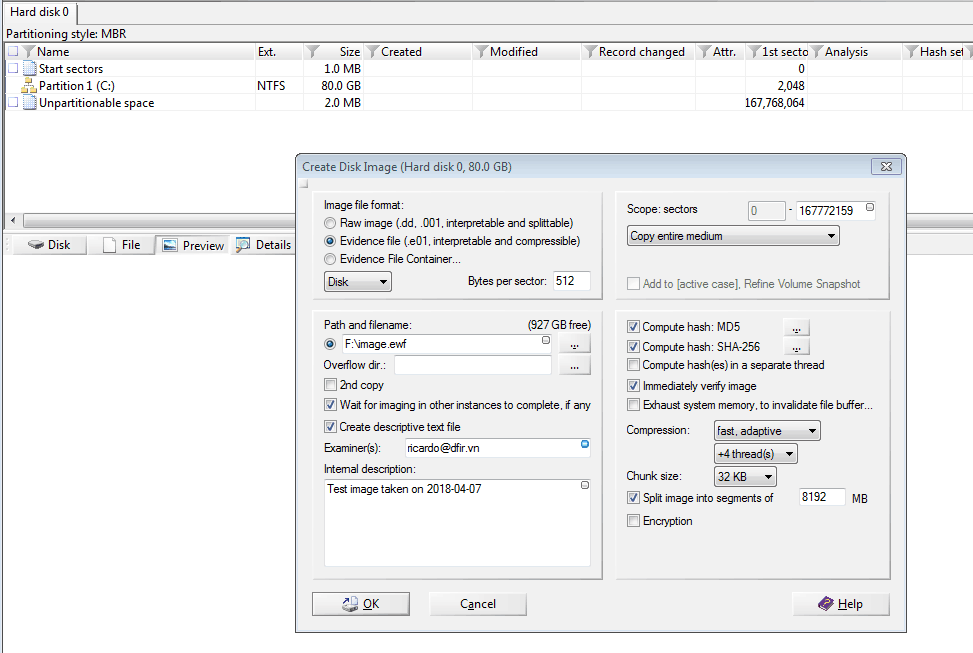
Forensic image example
After a forensic capture is complete on the imaging device, the image file, which is normally on EWF format, is verified with command line tools:
root@guymager:~# ewfverify DFIR20180306001.E01
ewfverify 20140608Verify started at: Mar 07, 2018 15:07:27
This could take a while.Verify completed at: Mar 07, 2018 15:07:28
Read: 290 MiB (304087040 bytes) in 1 second(s) with 290 MiB/s (304087040 bytes/second).
MD5 hash stored in file: db8ab7871bc2b7d456c4746e706fb5d3
MD5 hash calculated over data: db8ab7871bc2b7d456c4746e706fb5d3Additional hash values:
SHA1: 0dab4812fd1bb959e506d7ff6096bc9cb04d824aewfverify: SUCCESS
Once the verification is complete and the cryptographic hashes (in green) are confirmed, the forensic specialist will proceed to sign the image with the local forensic device key.
root@kit001:~# gpg –detach-sign –armor DFIR20180306001.E01
This creates a detached ascii encoded pgp signature on the same directory as the image (DFIR20180306001.E01.asc). We rename that to asc1, in order to specify that is the forensics kit signature.
root@kit001:~# ls -ltr
total 290228
-rw-r–r– 1 root root 297174413 Mar 7 12:36 DFIR20180306001.E01
-rw-r–r– 1 root root 6550 Mar 7 12:36 DFIR20180306001.info
-rw-r–r– 1 root root 488 Mar 7 15:11 DFIR20180306001.E01.asc1
The signature can be verified locally on the forensics kit (or anywhere else with access to the forensic kit public key list)
root@kit001:~# gpg –verify DFIR20180306001.E01.asc1 DFIR20180306001.E01
gpg: assuming signed data in ‘DFIR20180306001.E01’
gpg: Signature made Wed 07 Mar 2018 15:11:51 GMT
gpg: using RSA key B3F33C3EA502624797966B4E5ECD246796F91A8C
gpg: Good signature from “DFIR-KIT001 <kit001@dfir.vn>” [ultimate]
At this point, the removable media, typically a SATA 3.5 inch harddrive on a USB3/Firewire cradle is detached from the forensics kit and connected to the forensic investigator laptop.
ricardo@laptop /forensics/images/20180306 $ ls -ltr
total 290217
-rw-r–r– 1 ricardo ricardo 297174413 Mar 7 23:22 DFIR20180306001.E01
-rw-r–r– 1 ricardo ricardo 6550 Mar 7 23:22 DFIR20180306001.info
-rw-r–r– 1 ricardo ricardo 488 Mar 7 23:22 DFIR20180306001.E01.asc1
The first step is to verify the signature made at the forensics kit.
ricardo@laptop /forensics/images/20180306 $ gpg –verify DFIR20180306001.E01.asc1 DFIR20180306001.E01
gpg: Signature made Wed 07 Mar 2018 22:11:51 +07 using RSA key ID 96F91A8C
gpg: Good signature from “DFIR-KIT001 <kit001@dfir.vn>”
If this succeeds, the forensic investigator will sign the image with his own personal key.
ricardo@laptop /forensics/images/20180306 $ gpg –detach-sign –armor -u ricardo@dfir.vn DFIR20180306001.E01
You need a passphrase to unlock the secret key for
user: “Ricardo Gandara <ricardo@dfir.vn>”
4096-bit RSA key, ID 7593B7BC, created 2018-03-07
The file created will be renamed to asc2 in order to make clear that this is the investigator signature.
-rw-r–r– 1 ricardo ricardo 297174413 Mar 7 23:22 DFIR20180306001.E01
-rw-r–r– 1 ricardo ricardo 6550 Mar 7 23:22 DFIR20180306001.info
-rw-r–r– 1 ricardo ricardo 488 Mar 7 23:22 DFIR20180306001.E01.asc1
-rw-r–r– 1 ricardo ricardo 819 Mar 7 23:28 DFIR20180306001.E01.asc2
The image package is now complete. Both signatures can be verified at any time by anyone with access to the relevant public keys (which we publish onto public keyservers, like pgp.mit.edu or keybase.io).
ricardo@laptop /forensics/images/20180306 $ gpg –verify DFIR20180306001.E01.asc1 DFIR20180306001.E01
gpg: Signature made Wed 07 Mar 2018 22:11:51 +07 using RSA key ID 96F91A8C
gpg: Good signature from “DFIR-KIT001 <kit001@dfir.vn>”
ricardo@laptop /forensics/images/20180306 $ gpg –verify DFIR20180306001.E01.asc2 DFIR20180306001.E01
gpg: Signature made Wed 07 Mar 2018 23:28:15 +07 using RSA key ID 7593B7BC
gpg: Good signature from “Ricardo Gandara <ricardo@dfir.vn>”