- READ MORE
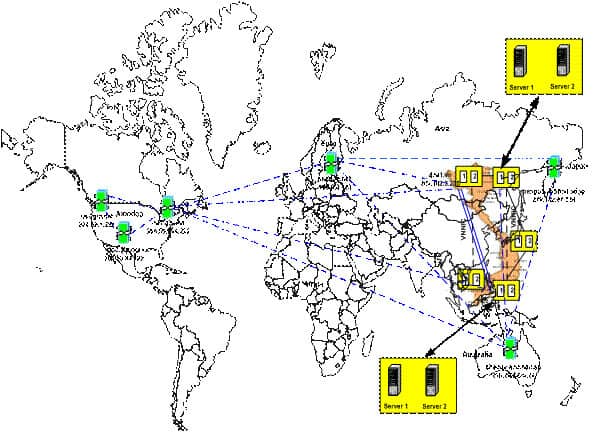
We regularly encounter scenarios where attackers gain unauthorised access to users’ mailboxes. The aim of the digital forensic examiner is to understand as much as possible about the breach in order to give to recommend the client which steps to take (how access was gained, how long was the breach undetected, whether emails were sent, […]