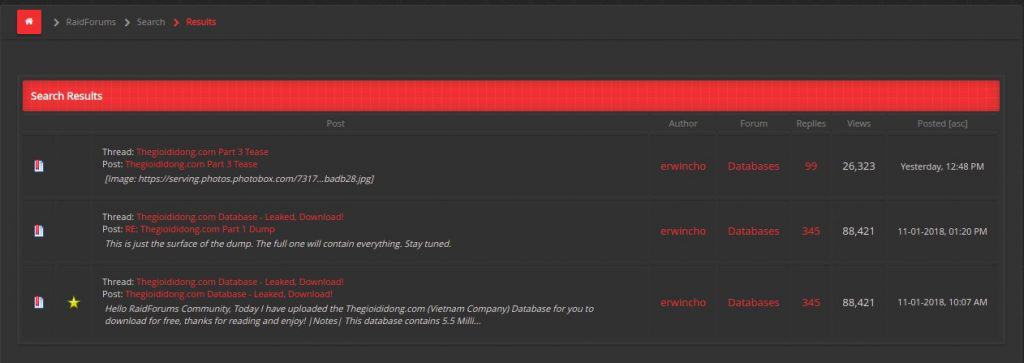
On November 1st 2018, a new user under the name “Erwincho” registered onto RaidForums – a well known site with over 150,000 members where users post leaked databases that have normally become publicly available elsewhere in hacking forums. His first step in the forum was to upload a database allegedly leaked from Thegiodidong.com, the Vietnamese electronics and white goods retailer, claiming to have compromised internal systems at the company and gained access to user databases and credit card details.
The response to the Erwincho’s posts was overwhelming, with many Vietnamese users quickly registering to the forum in order to ascertain whether their personal information had been leaked – which would lead to card cancellations, or personal details being leaked. So far, the three posts by Erwincho have over 700 replies, with over 200,000 views. It has definitely raised interest.
At the time of writing (November 8th) we estimate that Erwincho’s leak had been downloaded between 150 and 200 times.
The release has hit the local news with Tuoi Tre News reporting it on November 8th – leading to a spike on the forum readership. In the article the head of IT at The Gioi Di Dong has been reported confirming that the information is false – and that “Hackers might have obtained the addresses from other online sources and claimed that they belong to The Gioi Di Dong“. An official press release is also available – https://www.thegioididong.com/tin-tuc/the-gioi-di-dong-bi-ro-ri-thong-tin-khach-hang-do-la-tin-gia–1129601
At DFIR VN we decided to download the leak (that had been re-posted elsewhere in a MEGA link) and analyse it to see whether the The Gioi Di Dong claim that the leak is fake could be confirmed independently.
Dataset
The leaks consists of three files:
-rw-rw-r-- 1 dfir dfir 157913239 Nov 7 14:52 emails.txt -rw-rw-r-- 1 dfir dfir 4293666 Nov 7 14:57 transactions.txt -rw-rw-r-- 1 dfir dfir 2795165 Nov 7 15:04 tgdd-internal.txt
The first file “emails.txt” is just an email list containing 5427026 lines with an email per line. In true Raidforums fashion, the release has been tagged with two additional accounts watermarking the leak to the forum. The file contains no duplicates.
$ grep raidforums emails.txt secureyourhome@draidforums.net secureyourhomeadtauthco@draidforums.net
The second file “transactions.txt” is a CSV file with transaction information, including masked credit/debit card data. It contains a Vietnamese header on the first line.
Số hiệu thiết bị (TID),Số hiệu đơn vị (MID),Địa chỉ (Tên đơn vị),Loại thẻ,Ngày giao dịch,Giờ giao dịch,Ngày xử lý,Số thẻ,Mã chuẩn chi,Số lô,Số tiền giao dịch gốc,Phí (chưa VAT),VAT (của phí),Tỷ lệ phí (%),Số tham chiếu, 01024110,100000000015225,THEGIOIDIDONG.COM-1201,GENT,20160629,172623,20160701,970415******1915,022862,86886,445000,0,0,0,744622554, 01021546,100000000013713,DIENMAYXANH.COM-663,BNVN,20160629,172635,20160701,970436******4027,000000,86886,200000,364,36,0.2,744622751, 01022889,100000000014434,THEGIOIDIDONG.COM-1079,GENT,20160629,172640,20160701,970415******2244,047164,86886,615000,0,0,0,744622832, 01018793,100000000012198,THE GIOI DI DONG-887,MAST,20160629,172642,20160701,539146******3875,084729,86886,915000,9982,998,1.2,744622856, 01024110,100000000015225,THEGIOIDIDONG.COM-1201,GENT,20160629,172807,20160701,970415******1915,046211,86886,320000,0,0,0,744624202, 01024374,100000000015310,THEGIOIDIDONG.COM-1236,BNVN,20160629,172858,20160701,970436******5017,000000,86886,976000,1775,177,0.2,744624936,
The columns are:
- Số hiệu thiết bị (TID): Equipment number – it appears to be the reference for the card machine reading the transaction. It is not a primary – duplicates exist.
- Số hiệu đơn vị (MID): Unit number – Merchant IT
- Địa chỉ (Tên đơn vị): Address/unit name.
- Only 759 distinct (TID,MID, Địa chỉ) tuples exist.
- Loại thẻ: Card type (Mastercard, JCB..etc)
- Ngày giao dịch: transaction date in a YYYYMMDD format
- Giờ giao dịch: transaction time in a HHMMSS format
- Ngày xử lý: Processing date in YYYYMMDD
- Số thẻ: Card number with the middle 6 digits masked
- Mã chuẩn chi: Standard code
- Số lô: Lot number
- Số tiền giao dịch gốc : Original transaction amount
- Phí (chưa VAT): Charge (without VAT)
- VAT (của phí): VAT of charge
- Tỷ lệ phí (%): Rate of charge
- Số tham chiếu: Reference number
The third file “tgdd-internal.txt” is another list of emails with one email per line, this time containing only email that have the string “thegioididong” in it. The file contains 61523 records with no duplicates.
Analysis
Emails
The first point of research are the email domains used by the email list. We know from our analysis on our Cloud email usage article that most users in Vietnam will use Google Gmail and Yahoo for email. Is this leak the same?
The top 25 domains on the leak are:
| Domain | Number of entries |
|---|---|
| yahoo.com | 1307725 |
| gmail.com | 1195112 |
| hotmail.com | 371579 |
| amazonses.com | 173482 |
| yahoo.com.vn | 56299 |
| mandrillapp.com | 55586 |
| msn.com | 52091 |
| firstscotia.com | 51475 |
| maestro.bounces.google.com | 51108 |
| bounce.linkedin.com | 48139 |
| thegioididong.com | 42142 |
| comcast.net | 34856 |
| sbcglobal.net | 33766 |
| us-west-2.amazonses.com | 26345 |
| ymail.com | 25677 |
| att.net | 25095 |
| verizon.net | 24240 |
| bellsouth.net | 18439 |
| live.com | 13823 |
| earthlink.net | 13255 |
| yahoo.co.uk | 13083 |
| charter.net | 11131 |
| bounce.agoda-emails.com | 10391 |
| yahoo.com.br | 10267 |
| outlook.com | 10157 |
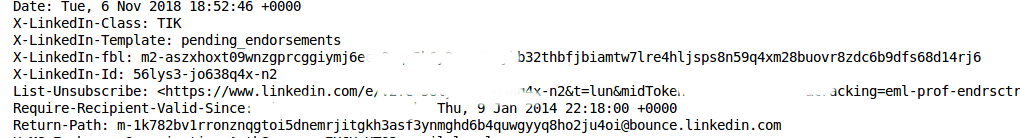
The list does not look right. Yes, yahoo, gmail and hotmail are the three most prominent providers, but a lot of the domains used like amazonses.com, mandrillapp.com are used for mailing list management. Several of the domains are actually explicit “Return-Path” bounce emails from LinkedIn (bounce.linkedin.com) , Google (maestro.bounces.google.com) and Agoda (bounce.agoda-emails.com).
For example a bunch of the LinkedIn emails does indeed looks exactly like the Return-Path header of a LinkedIn marketing message:
m-0e6eje8balhs5zkyyngypjyfp1yekz8mwmw4wktrwedkebvp1nebicppknf-@bounce.linkedin.com m-0escv1hh0xm-s2xtiykluvqgew-sr2pa36_pihzt_xj3bif2kypwzi8crfok@bounce.linkedin.com m-0j7rgt4ko529edfvpyzacjbeiyiiyglcwhx8ri4fn6-lwoqaykeifiz19ahu@bounce.linkedin.com m-0mfttinwkzvp2ony1qo7tyc5vfepuitm5hxdged3aq_0tfopyqzxvtmmsseu@bounce.linkedin.com m-0ne7ej2simib0u-_j2otj2ep8vqewrvneiriet2wac2km98dj26ueepwyk0y@bounce.linkedin.com m-0shacnvrnqqelgfx1a4ztj1ibvcmdgab53frnipuphkicexfyaeo6hzlpb_r@bounce.linkedin.com
So, this list is not a user database. Maybe emails automatically extracted with a badly put together script from an email server spool – that would have catch all the headers including the bounces.
But there are a lot of emails, and some of the domains (att.net, yahoo.com.br…etc) are not your average Thegioididong customers. Some of them are plain implausible as The Gioi Di Dong’s customers like “www.jeffersondossantosaguiar@yahoo.com.br” or “123sexygirl@yahoo.com”.
On the evidence, we can say that this email leak has been “stuffed” with bad credentials. There may be a few accounts valid in the leak (a few hundreds or thousands), but this has been padded extensively in order to make the list appear to be millions.
Transactions
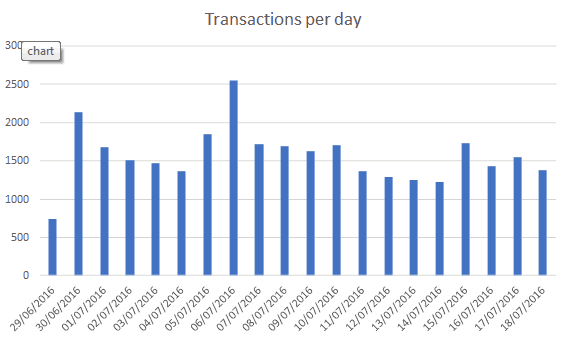
The second point of research is the transactions CSV file. It is very detailed. The transactions processing dates are all in July 2016 with the first one being on July 1st and the last one on July 19th. It contains 31247 transactions – which are between 1200 and 2500 per day.
But the intriguing part is the “Card”, “Original Transaction Amount”, “Charge”, “VAT of charge” and “Rate of Charge”. These would be typically amounts charged by a Payment processor. For example, the line “BNVN,1111000,2020,202,0.2” indicates that a card of type BNVN (Bank Vietnam), of an original transaction of 1,110,000 VND, a commission of 0.2% + VAT (2020 + 202 VND) was charged.
The rates of charges depends on the card type and bank issuer. The bank issuer can be detected by looking at the six numbers of the card (which are unmasked). A quick lookup can be done at Binlist.net (https://binlist.net/), which will offer details on credit cards – local Napas-type cards are not recognised.
These appear to be real transactions. The largest amount spent was 85 million VND, and the smallest a refund of -11 million VND. The most common payment were 190,000 VND (733 times) and 1,000,000 VND (605 times).
The transaction file comes from 759 different equipment. The equipment identifiers have the TID and MID acronyms. TID is the Terminal Identification, MID is the Merchant Identification in the payment processing industry.
TID, MID, Unit name 01022612,100000000014233,THEGIOIDIDONG.COM-210 01008020,100000000005903,THEGIOIDIDONG.COM-310 01010535,100000000007495,THEGIOIDIDONG.COM-410 01012937,100000000009042,THEGIOIDIDONG.COM-510 01000241,100000000000212,THEGIOIDIDONG.COM-710
These are card readers. Some units (likely shops) have more than one terminal, but the same address and (at times) same merchant id.
01018736,100000000012158,DIENMAYXANH.COM-630 01018737,100000000012158,DIENMAYXANH.COM-630 01024964,100000000015665,DIEN MAY XANH.COM-1011 01024965,100000000015665,DIEN MAY XANH.COM-1011
The codes at the end of the line indicate that these are different retail shops across the country.
The leak appears to have originated from the payment processing system that handles the physical card payment. However that system does not appear to have any user information (only handles card transactions – separate from the TGDD backoffice system).
Another problem is that all transactions have reference numbers at the end of the line.
01024110,100000000015225,THEGIOIDIDONG.COM-1201,GENT,20160629,172623,20160701,970415******1915,022862,86886,445000,0,0,0,744622554, 01021546,100000000013713,DIENMAYXANH.COM-663,BNVN,20160629,172635,20160701,970436******4027,000000,86886,200000,364,36,0.2,744622751, 01022889,100000000014434,THEGIOIDIDONG.COM-1079,GENT,20160629,172640,20160701,970415******2244,047164,86886,615000,0,0,0,744622832, 01018793,100000000012198,THE GIOI DI DONG-887,MAST,20160629,172642,20160701,539146******3875,084729,86886,915000,9982,998,1.2,744622856, 01024110,100000000015225,THEGIOIDIDONG.COM-1201,GENT,20160629,172807,20160701,970415******1915,046211,86886,320000,0,0,0,744624202,
If we order by these transaction ids we can see the following:
- Negative value transactions (refunds) have no reference numbers
- The sequence has plenty of gaps in between transactions. The system these values have been taken from processes a lot more transactions than just these few. Example: 758179058, 758179268, 758179517, 758179872,758179915
This is not a full system dump of a point of sale system (which should not/would not store card numbers anyway). This is likely to be a merchant report from a card payment provider.
Summary
Few attackers would waste current (valid) credit cards on Raidforums – as there are many dark web marketplaces where card details could be sold at a profit.
Given the quality of the email lists taken – very likely extracted with a script from a raw email dump- with credential stuffing, with the additional release of this July 2016 report from The Gioi Di Dong’s card payment provider, it is possible that the attackers gained access to one or several email accounts at The Gioi Di Dong (one containing the report as an email attachment). Access to the upstream payment provider would have been a larger issue – unlikely to have been wasted on a Raidforums release.
So far, nothing indicates that the information released originates from confidential back-office systems.