-
Digital Forensics / Media forensics / Network Forensics April 19, 2018
READ MOREAll forensic investigators need a travel forensics kit. This is a set of equipment you can grab at a short notice that should cover “most” eventualities when at an engagement. Typical components are a forensic workstation with the relevant software, write blockers, network taps, external storage, and other tools.
- READ MORE
On many cases a forensics investigation has to be done quickly and without affecting systems hosting live data without affecting the current workload, or preventing users from accessing the system. DFIR has processes to obtain the best possible forensics data in this situations.
- READ MORE
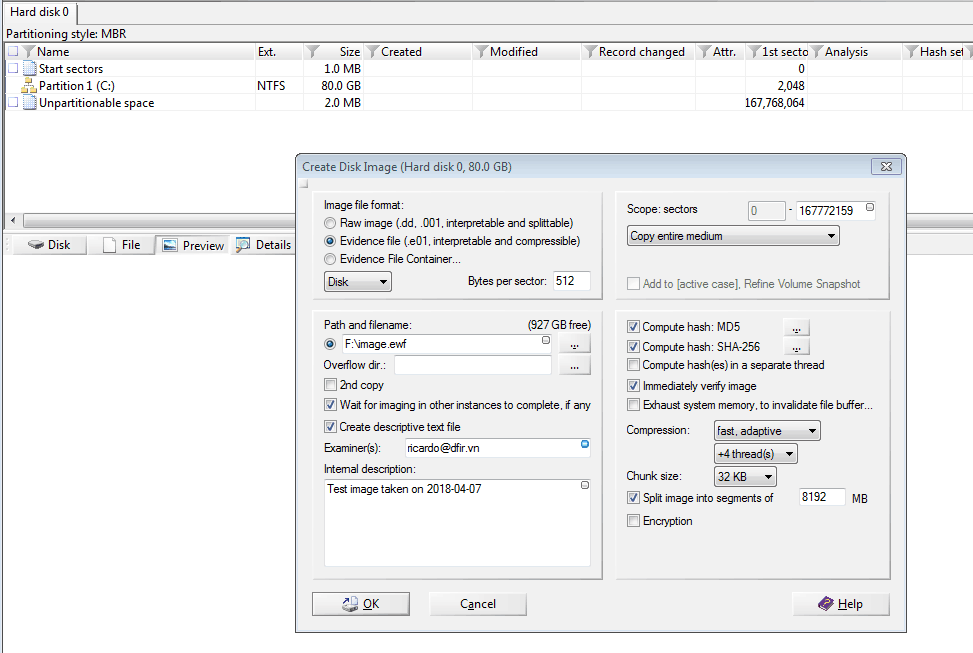
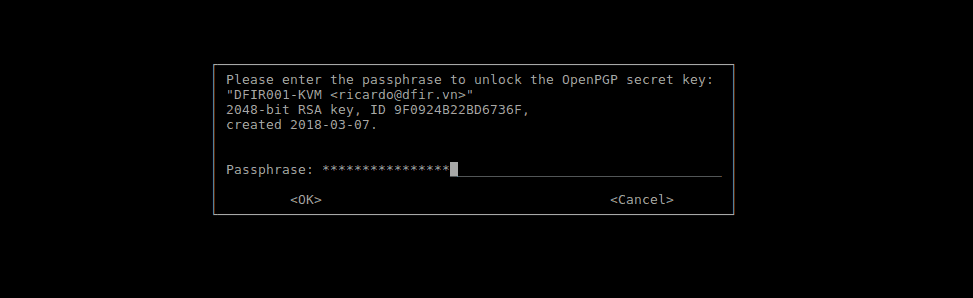
In order to ensure the images we create are tamper-proof (can not be switched/replaced or modified), we use digital signatures using GPG (https://www.gnupg.org/). DFIR VN runs a double signature system for forensic captures.
- READ MORE
One of the most useful things a local IT department can do when confronted with a security event is capture information. A fresh dataset, captured hours or days after an event can be crucial in order to answer important questions at a later stage. Once captured in a standard manner, the digital footprints are “frozen” […]
- READ MORE
A place where evidence handling shines on Linux is the ability to safely mount full disk images using loopback devices. This post will explain how to simply mount the different partitions within a read-only image and then access different Virtual Shadow Copies (VSS) for NTFS partitions.
- READ MORE
Autopsy is a digital forensics and graphical interface to The Sleuth Kit and other forensic tools (https://www.sleuthkit.org/autopsy/).