Weak passwords are an easy way attackers use to get into systems or networks. All internet exposed servers, website login forms and email addresses are constantly being scanned by automatic scripts trying to “guess” passwords. If any of your passwords are easy to guess, or on the “most common” lists, your organization will have a breach soon.
Attack types
From a network defense and incident response perspective, the question is to understand which credentials are routinely tried to break into accounts (so we can avoid using them). These are of two types:
- Non-targeted attacks: These use lists of most common passwords that are widely available. There are many of such lists available, with the best source being SecLists (https://github.com/danielmiessler/SecLists) by Daniel Miessler and Jason Haddix.
- Targeted attacks: These use lists of already compromised credentials for a particular organization. This is a problem in large companies, where staff members may use the same corporate email and associated password to create third party accounts (Instagram, Zalopay…etc). If Instagram or Zalopay gets hacked and the password falls into the wrong hands, attackers will attempt to reuse them on corporate services.
These two types are related, the list of most common passwords are generated by aggregating hundreds of database leaks. However looking at the current top 15 most commonly used passwords (at the time of writing – May 2018) we have: [111111, 1234, 12345, 123456, 1234567, 12345678, abc123, dragon, iloveyou, letmein, monkey, password, qwerty, tequiero, test]. At first sight, this list is very US centric (all words are English or Spanish). So at DFIR VN labs, we asked ourselves the question:
“what are the most common passwords used by Vietnamese speakers?”
Surely it will contain Vietnamese words or be based around numbers as users find vietnamese special characters and tones difficult to type on password fields (as autocorrect can not be used).
Vietnamese leaked credentials
Where to start? Leaked credentials on the .vn TLD are rare. The most common domain name seen on historic leaked credentials is “yahoo.com.vn” and those leaks are under 0.04% of all accounts leaked worldwide (barely 1.2 million accounts our of 3.5 billion leaks worldwide on the DFIR VN lab databases). Other common domains are zing.vn (with 70,000 leaks) and gmail.com.vn (with about 20,000). This is quite common, as most users will use email addresses that are not on the .vn TLD (gmail.com…etc). This would, of course, prevent any analysis, as we will have no way to know whether those users are Vietnamese or not (without additional information).
But this changed at the end of April 2018 (barely 5 days before this article was written).
As reported in the local news, a large database with 163 million credentials was leaked form VNG Corporation (https://tuoitrenews.vn/news/business/20180428/vietnams-tech-giant-vng-apologizes-after-alleged-data-breach-affecting-163mn-accounts/45340.html). This is quite a large breach and the corpus (for a total of 34GB, now publicly available in torrent sites and database leaks forums) is big enough to perform some statistical analysis.
Not all accounts on the set contained email addresses, as the majority of the accounts only had usernames. Only 25 million distinct emails were on the database. For individual users, if you want to check whether your account is within that 25 million subset you should check the excellent site “Have I been pwned” run by Troy Hunt, who added the VNG dataset barely two days after the leak was published.
A sample of the lines retrieved (with heavy redactions to mask confidential information) is below:
84988484,[redacted],504865,25F9E794323B453885F5181F1B624D0B,,[redacted],13,quehuong,1,789456123,1955-08-24 00:00:00.0,63,[redacted]6789,ha nam,,18,,2010-05-28 10:20:58.813,21,2010-05-28 10:16:35.86,,98560,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, 84988485,[redacted],768,43B405A57C86F22A06ABD75824B841E5,,,,,,,,,,,,,,,,,2010-05-28 09:36:05.893,3,2010-05-28 09:36:05.893,,768,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, 84988511,[redacted],1570337,E36A2F90240E9E84483504FD4A704452,06DC67758E6BD6F8B089AEE4A915441E,[redacted],16,d9b8e8f09aea13fab32b8b75dce76192,1,b[redacted] 84988670,[redacted],768,E807F1FCF82D132F9BB018CA6738A19F,,,,,,,,,,,,,,,,,2010-05-28 08:23:50.237,50,2010-05-28 08:23:50.237,,768,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, 84988734,[redacted],390689,B461C2E02715AFCE5A69C861D468A285,5D5F9EAE00052AE36A35DEE977902BB8,[redacted],13,00c0498b0603bc0b3e72446ae5f41ec9,1,[redacted]1992-10-29 00:00:00.0,,ha noi,,43,,2011-12-09 18:09:22.907,56,2010-05-28 08:14:46.69,,768,0,2,,,,,,,,2011-12-09 18:08:50.357,2011-12-09 18:08:50.357,,,,,,,,,,,,,,,,,,,, 84988778,[redacted],768,D6CD7880933606CAB470D822596E20DC,,,,,,,,,,,,,,,,,2010-05-28 15:20:54.233,5,2010-05-28 15:20:54.233,,768,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, 84988863,[redacted],768,25F9E794323B453885F5181F1B624D0B,,,,,,,,,,,,,,,,,2010-05-28 05:59:28.317,16,2010-05-28 05:59:28.317,,768,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, 84988885,[redacted],1555491,30047333851ED60047066A5FD566C11A,,[redacted],10,205d183506fb596a2cebc399d72a3d28,,012782037,,,[redacted],00:00:00.0,01262262201,[redacted],,43,,2012-07-04 12:27:20.81,38,2010-05-28 06:55:08.05,,98560,1,8,,,,,,,,2011-12-22 10:40:10.92,2011-07-18 17:16:12.103,2011-12-22 10:52:53.21,,,,,,,,,,,,,,,,,,,
Marked in bold are the passwords as encoded on the VNG database. Unfortunately for VNG users the passwords were stored using the MD5 algorithm. This algorithm is quite old (design by Ron Rivest in 1991) and has the advantage of being very fast. The operation to verify that the string “password” corresponds to the MD5 encoding “5f4dcc3b5aa765d61d8327deb882cf99” takes a minuscule amount of time on modern hardware. Optimized programs running on graphics cards (CUDA, OpenCL) can easily calculate about 1 billion hashes per second.
However, this blazingly fast speed is NOT a good thing when safely storing passwords. While the service authenticating users will go slightly faster (and probably will save a few seconds of CPU power per day), if the database is leaked, attackers can then bruteforce the list with dictionaries at very high speeds. A better choice for password algorithm would be Argon2 (which was the winner of the 2015 Password Hashing Competition), pbkdf2 or bcrypt (which have more widespread library support). This algorithms are purposedly slower to prevent attackers from succesfully obtaining the decoded passwords.
Dehashing the VNG database
A quick analysis on the VNG database showed that password reuse was very common. The 163 million accounts only used about 33.8 million distinct passwords. These hashes were extracted on to a separate list.
Once the hashes have been extracted from the database we needed to brueoforce them. The most efficient way is to use hashcat on a system with a suitable graphics card. For this exercise we used (in order to limit ourselves) to 24 hours’ worth of Amazon Web Services time p2.xlarge which runs a single Nvidia K80 GPU. The cost of the exercise was $0.30 per hour, so approx 175,000 VND in total for the day.
On those 24 hours we did run several cracking sessions with different settings and dictionaries. The average cracking speed was 250 million MD5 hashes per second.
Session..........: hashcat Status...........: Exhausted Hash.Type........: MD5 Hash.Target......: ../VNG_md5.txt Time.Started.....: Mon Apr 30 17:09:20 2018 (13 hours, 21 mins) Time.Estimated...: Tue May 1 06:30:34 2018 (0 secs) Guess.Base.......: File (../wordlist/passwordlist.txt) Guess.Mod........: Rules (rules/OneRuleToRuleThemAll.rule) Guess.Queue......: 1/1 (100.00%) Speed.Dev.#1.....: 227.5 MH/s (1.08ms) @ Accel:32 Loops:16 Thr:512 Vec:1 Recovered........: 16589604/33808350 (49.07%) Digests, 0/1 (0.00%) Salts Recovered/Time...: CUR:1813,112731,N/A AVG:15002,900130,21603142 (Min,Hour,Day) Progress.........: 12382037305000/12382037305000 (100.00%) Rejected.........: 0/12382037305000 (0.00%) Restore.Point....: 238139000/238139000 (100.00%) Candidates.#1....: $HEX[7a756b616969613537] -> $HEX[f67a6c656d2a] HWMon.Dev.#1.....: Temp: 67c Util: 66% Core: 875MHz Mem:2505MHz Bus:16 Started: Mon Apr 30 16:55:24 2018 Stopped: Tue May 1 06:30:36 2018
The end result was that 22.3 million distinct passwords were cracked (65.9% of the total of distinct passwords). Given that the most common passwords are typically easier to guess, the list obtained did correspond to which did also correspond to 131.9 million credentials on the full list (81% of all accounts).
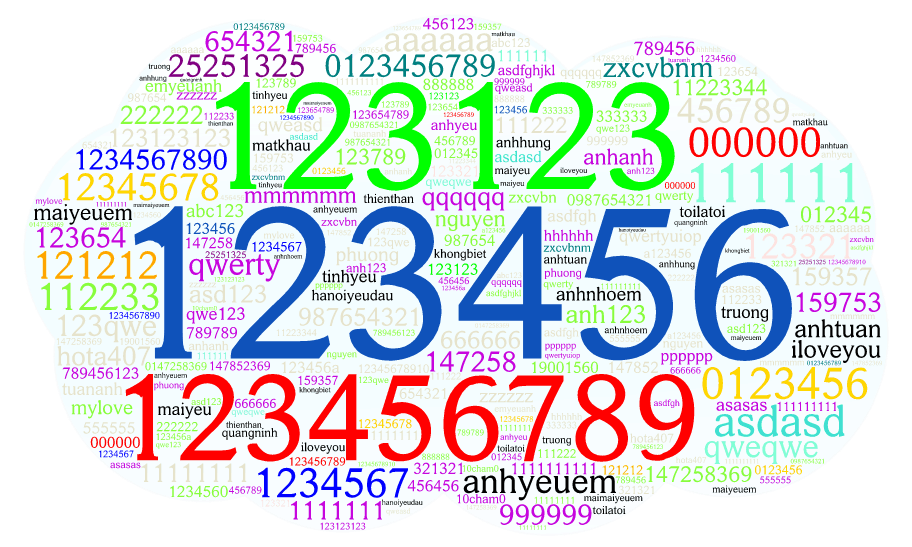
So, what are the most common 100 passwords on this Vietnamese-centric leak:
| Rank | Password | Frequency (percentage) |
|---|---|---|
| 1 | 123456 | 12.24% |
| 2 | 123456789 | 3.15% |
| 3 | 123123 | 1.65% |
| 4 | 111111 | 1.02% |
| 5 | anhyeuem | 0.57% |
| 6 | 1234567 | 0.51% |
| 7 | 0123456789 | 0.43% |
| 8 | 0123456 | 0.33% |
| 9 | 12345678 | 0.32% |
| 10 | 000000 | 0.26% |
| 11 | asdasd | 0.24% |
| 12 | 25251325 | 0.23% |
| 13 | 1234567890 | 0.23% |
| 14 | 121212 | 0.16% |
| 15 | 123321 | 0.16% |
| 16 | zxcvbnm | 0.15% |
| 17 | qweqwe | 0.12% |
| 18 | 456789 | 0.12% |
| 19 | 112233 | 0.12% |
| 20 | aaaaaa | 0.12% |
| 21 | 123123123 | 0.11% |
| 22 | 987654321 | 0.10% |
| 23 | 11111111 | 0.10% |
| 24 | qwerty | 0.10% |
| 25 | 147258369 | 0.10% |
| 26 | maiyeuem | 0.09% |
| 27 | 123qwe | 0.09% |
| 28 | 654321 | 0.09% |
| 29 | iloveyou | 0.09% |
| 30 | 123654 | 0.08% |
| 31 | 999999 | 0.08% |
| 32 | qqqqqq | 0.08% |
| 33 | 1111111 | 0.07% |
| 34 | 147258 | 0.07% |
| 35 | hota407 | 0.07% |
| 36 | anhtuan | 0.06% |
| 37 | 222222 | 0.06% |
| 38 | 159753 | 0.06% |
| 39 | 11223344 | 0.05% |
| 40 | anhnhoem | 0.05% |
| 41 | anh123 | 0.05% |
| 42 | 159357 | 0.05% |
| 43 | qwertyuiop | 0.05% |
| 44 | asd123 | 0.05% |
| 45 | 0987654321 | 0.05% |
| 46 | emyeuanh | 0.05% |
| 47 | mmmmmm | 0.05% |
| 48 | 12345 | 0.04% |
| 49 | 666666 | 0.04% |
| 50 | anhanh | 0.04% |
| 51 | 123789 | 0.04% |
| 52 | phuong | 0.04% |
| 53 | 111222 | 0.04% |
| 54 | qweasd | 0.04% |
| 55 | hanoiyeudau | 0.04% |
| 56 | nguyen | 0.04% |
| 57 | 789456 | 0.04% |
| 58 | 1111111111 | 0.04% |
| 59 | mylove | 0.04% |
| 60 | 789456123 | 0.04% |
| 61 | 19001560 | 0.04% |
| 62 | qwe123 | 0.04% |
| 63 | asdfghjkl | 0.04% |
| 64 | pppppp | 0.04% |
| 65 | anhhung | 0.04% |
| 66 | 1234560 | 0.03% |
| 67 | abc123 | 0.03% |
| 68 | maiyeu | 0.03% |
| 69 | 123456a | 0.03% |
| 70 | zzzzzz | 0.03% |
| 71 | quangninh | 0.03% |
| 72 | 987654 | 0.03% |
| 73 | 555555 | 0.03% |
| 74 | tuananh | 0.03% |
| 75 | asasas | 0.03% |
| 76 | asdfgh | 0.03% |
| 77 | zxcvbn | 0.03% |
| 78 | 321321 | 0.03% |
| 79 | tinhyeu | 0.03% |
| 80 | 147852369 | 0.03% |
| 81 | 456123 | 0.03% |
| 82 | matkhau | 0.03% |
| 83 | 147852 | 0.03% |
| 84 | 12345678910 | 0.03% |
| 85 | thienthan | 0.03% |
| 86 | anhyeu | 0.03% |
| 87 | 111111111 | 0.03% |
| 88 | toilatoi | 0.03% |
| 89 | 10cham0 | 0.03% |
| 90 | 0147258369 | 0.03% |
| 91 | 456456 | 0.03% |
| 92 | khongbiet | 0.03% |
| 93 | 789789 | 0.03% |
| 94 | a123456 | 0.03% |
| 95 | 333333 | 0.03% |
| 96 | 888888 | 0.03% |
| 97 | 123654789 | 0.03% |
| 98 | truong | 0.03% |
| 99 | maimaiyeuem | 0.03% |
| 100 | hhhhhh | 0.03% |
We can see the following patterns:
- Numeric passwords (52 out of 100), typical as tones are historically not used in passwords due to character set incompatibilities.
- ASCII patterns (16 out of 100): nonsensical patters, either keyboard rows walks or letter repetition
- Vietnamese phrases (21 out of 100):
- anhyeuem at #5
- maiyeuem at #26
- anhtuan at #36
- annhoem at #41
- emyeuanh at #46
- Only 2 english phrases (mylove and iloveyou) appear on the top 100 list.
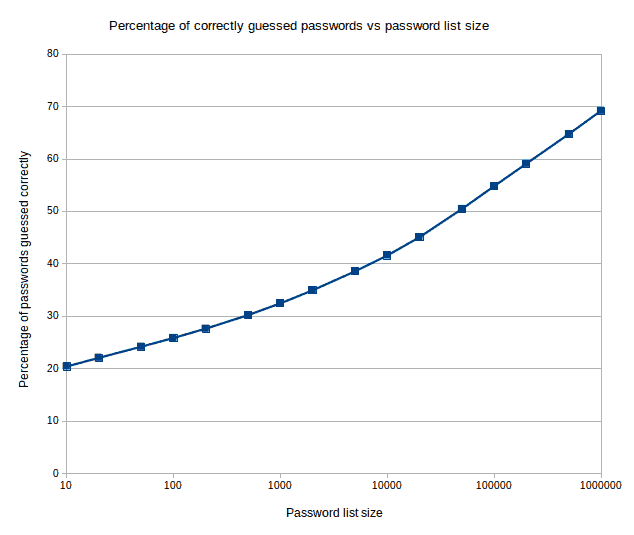
- The top 100 most common passwords cover 42.3 million credentials, the top 1000 cover 53.6 million credentials. In a logarithmic graph we can see that the 50% threshold is crossed on a 50,000 password list.
The full set of lists generated are available on our Github repository.
Recommendations
The large use of numeric passwords in Vietnam makes guessing passwords very easy. Attempting to log in with the top 500 passwords would approximately break into 33% of accounts (1 in 3).
This a marked cultural difference with English based password lists. On those, numeric passwords are in use at a much reduced rate (10-20%). For example, the 2017 English top 100 passwords list by Slashdata only has 14 numeric passwords. Additionally, bruteforcing numeric only passwords is a lot less complex, given that we have a smaller set of 10 characters to build a password [0-9] than the full alphanumeric upper/lowercase of 62 [0-9a-zA-Z]. Once could bruteforce all possible 16 digit numbers in a few hours on a single graphics card.
So, what could Vietnamese internet users do to consistently avoid bad passwords?
For individuals:
- Use a password manager (even on mobile devices). At DFIR VN we recomment Keypass for individuals and 1Password for teams. Both support mobile devices. These will generate random complex, virtually uncrackable passwords for any service.
- Use two factor authentication (SMS, numeric codes using Google Authenticator or a physical key like a Yubikey).
- Keep track of data breaches subscribing to services like “‘;–have I been pwned?” run by Troy Hunt.
For companies:
- Create a written password policy for the company. A good start is the latest NIST recommendation SP800-63-3 which removes the need for regular password changes and no more complexity rules, but at the expense of password audits and an 8 character minimum limit.
- Perform password audits using common lists like the ones shared in this article. Attempt to break into those accounts yourself before malicious actors do and trigger automatic password changes if they are in use. “Hack yourself first”.
- Make password bruteforcing difficult (use rate-limiting mechanisms) on those services exposed. Block further attempts after 10 failed logins for a period of time, block logins from non-standard IP addresses…etc.
For application developers:
- Store passwords securely. Do not store passwords in plaintex, or using MD5 or SHA functions. Use argon2, bcrypt or pkbdf2 to encrypt and store passwords (https://github.com/riverrun/comeonin/wiki/Choosing-the-password-hashing-algorithm).
- Integrate password lists with your backend services to prevent users from setting common passwords that have already been leaked online. You can use our lists or other lists available like the Pwned Password v2 list.
In short, password based security in Vietnam appears to be a lot weaker than initially thought. Vietnamese users (companies, developers and individuals) should take some of the easy measures outlined here in order to prevent further problems.