On many cases a forensics investigation has to be done quickly and without affecting systems hosting live data without affecting the current workload, or preventing users from accessing the system. DFIR has processes to obtain the best possible forensics data in this situations.
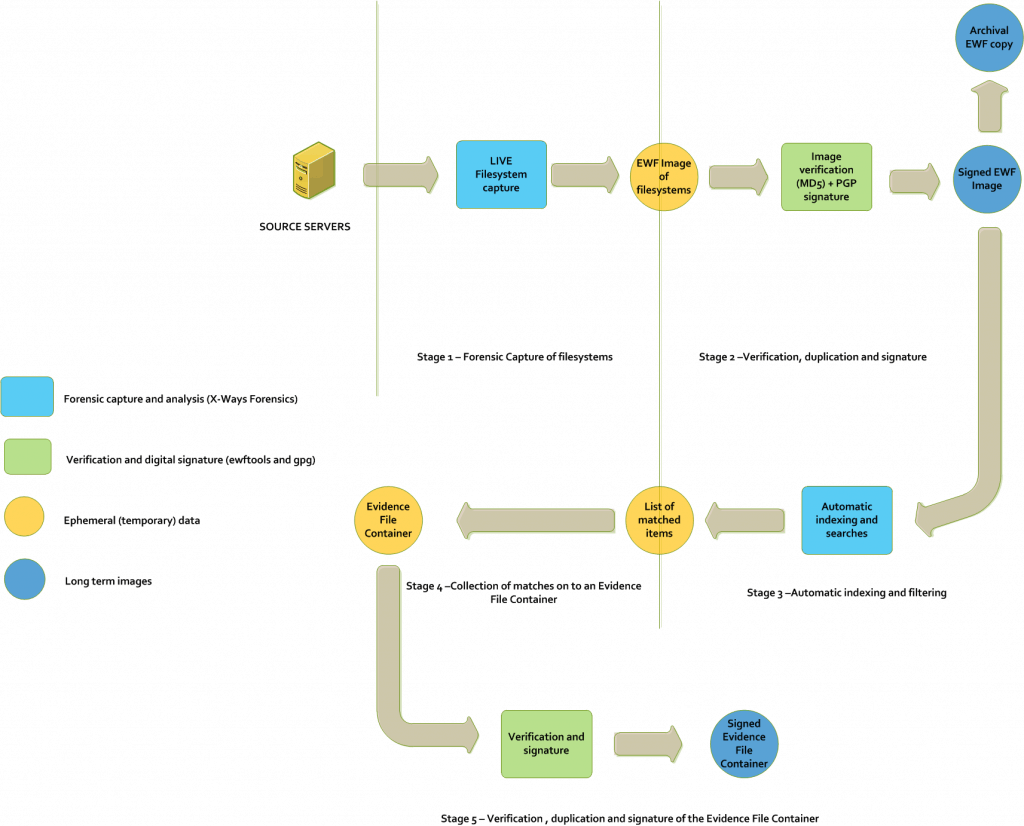
Our methodology in these cases is to take live forensic capture. This requires administrative access to the machine in question (local Administrator on windows based machines), root on Linux/Unix machines…etc. The DFIR processes used take a “live” copy of the filesystems, and optionally a live “image” of the system memory (if malware activity is suspected). That information is then stored on an image in the Expert Witness format and then signed and verified on the usual DFIR forensic capture processes.
On a windows environment (either 32 or 64 bits), that could host a large filesystem (file servers, email servers) we would likely use X-Ways Imager to perform the live capture.
The images will be processed on a data pipeline. In most cases, the investigation will be performed on a particular set of keywords that act as “leads” for the investigation. The keywords provide a filter in order to narrow down the items of interest. Once data is filtered and cut down to a manageable size it could be taken away from further processing.
The pipeline in question looks like the figure below: