As seen in our Vietnam cloud email study, 17% of all email infrastructure on the Vietnam DNS top level domain (.vn) is based on Google cloud. Google cloud email (also known as GSuite) is the single largest provider of email cloud services in Vietnam, being 5 times larger than the second largest provider – Zoho.
For custom domains (not the free accounts at gmail.com), the Google email offer is based on G Suite (formerly called Google Apps). There are three available service levels at different prices:
- Basic ($5/user/month)
- Business ($10/user/month): Basic + unlimited cloud storage + smart search + archive retention + user activity tracking
- Enterprise ($25/user/month): Business + data loss prevention +S/MIME encryption + email archiving + advanced electronic discovery settings
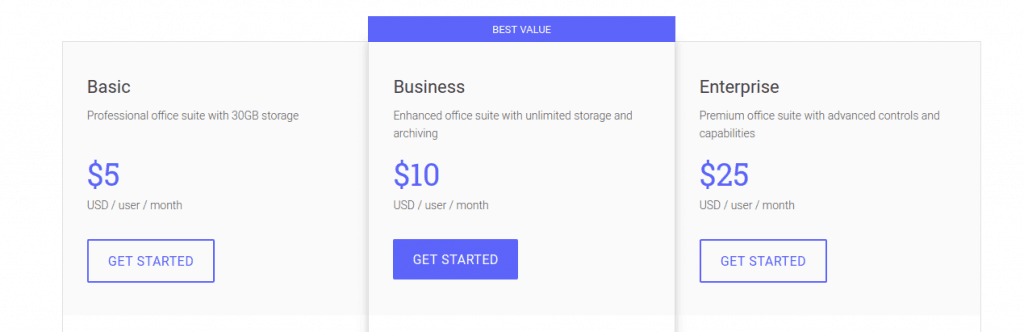
A complete list of features is here.
But, how do these features affect forensic investigations? DFIR VN often finds situations where email accounts are suspected to have been broken into by unauthorised users. How much information about each account does Google email make available? This article studies a similar setup on one of our domain names (dfir.com.vn).
The typical breach accesses a mailbox via webmail, as configuring an email client or a mobile device causes a lot more points of information to be tracked. As forensic investigators we are interested in anything that can help us monitor this:
- Per mailbox Session tracking (user, source IP address, timestamp, any information about connected devices – User Agents)
- Log retention, specifically how many days of logs are available at any point in time.
- Type of events logged (login success/failure, password changes…etc).
GSuite Basic provides all this however, the information has to be collected at different points.
The first point of call is for the individual user to check its own activity list, accessible from the main Gmail screen on a small link on the bottom right (see green spot)
From there a pop-up screen will appear with the last sessions available. However this is limited to the last 10 sessions with an exception of 3 “suspicious” sessions, if any.
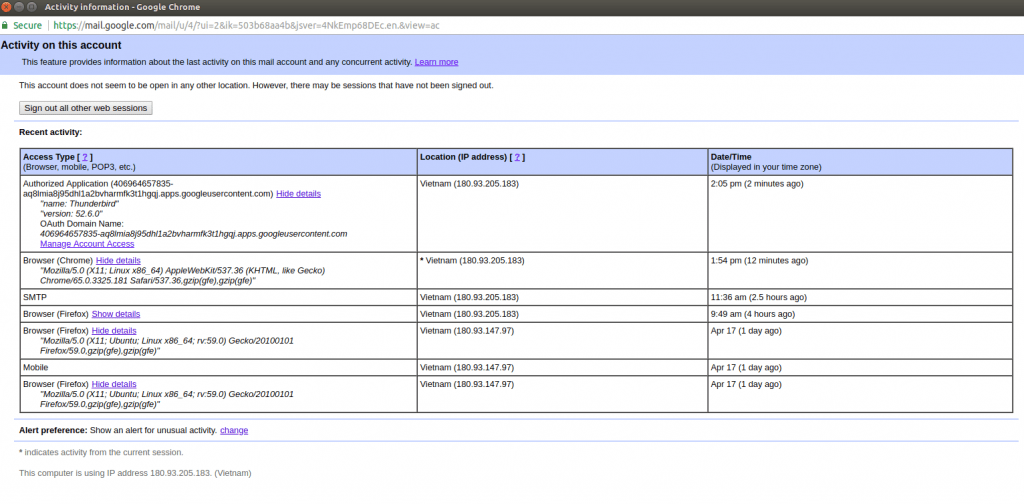
The list will contain:
- Any browser based sessions (webmail) with the full User Agent (which will indicate OS, browser version) and source IP address. Indicated by the last time the screen was refreshed or user logged in.
- Any authorized applications (typically email clients connecting via POP3 or IMAP). The time will be one the last known connection and will contain the name of the email client (but no operating system). The email client can be disconnected here.
- Accesses from mobile devices, however the details here are very limited. There is no make/model or even last seen timestamp on the list. This is compensated by My Account – “Device Activity & Security Events”, which has a much more detailed view. However this is not of any consequence on typical forensics cases, as attackers tend to use webmail to access compromised accounts, in order to give out as little information as possible.
| Pros | Cons |
|---|---|
| Users themselves can view this information | No easy way to download the information, apart from taking screenshots of the window. |
| The information is immediately available ("minutes ago") | The limit of 10 sessions (and 3 extra "unusual" ones) will give a very limited view (2-3 days max) of accounts with normal usage. |
The second point of all is the Report Administration interface of GSuite. This is only reachable via one of the GSuite organisation administrators. The left side many has the following options:
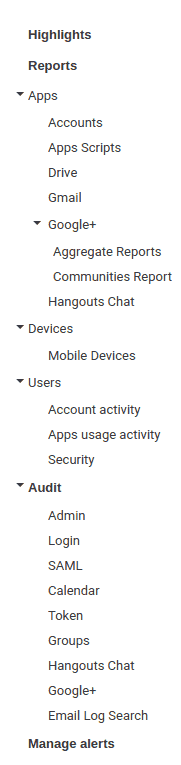 | All reports can be either downloaded as a CSV file or exported to Google Sheets. Exported CSV are in plain ascii format, trying to decode them in UTF-16 will lead to an incorrect character set. The fact that they can be easily exported makes life a lot easier for the forensic analysis. However, there is no place to get a single unified archive with all reports, so they have to be downloaded separately. However there is a downside to the admin console. While the individual user activity screen is available immediately, the majority of administration reports are delayed ("lagged") by 1 to 3 days (Info here) However, all the relevant data required for a forensic investigation is available quickly (under 30 minutes):
|
Other areas on the report tab are interesting only from a statistical perspective. The 3-day delay is fine here. Log retention is stated to be 6 months with 30 days for email log search and 15 months for usage data (https://support.google.com/a/answer/7061566).
All this information is available on a Basic account, which appears to be the most common choice for Vietnamese organizations. But do the Business and Enterprise offerings add anything to Digital forensics on a GSuite enabled domain?
A review of the support panel reveals that, rightly so, the email forensic capability is available on Basic. Business/Enterprise do provide two new interesting areas added to the Audit menu: Drive and Mobile Devices
| Basic | Business |
|---|---|
 | 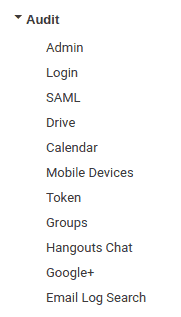 |
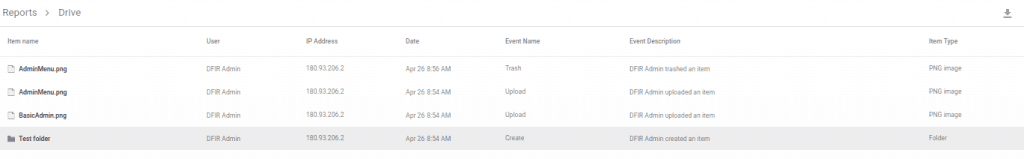
The Drive menu gives an immediate account of anything happening to the organization Google Drive folders. This has good forensic information, IP addresses, timestamps, usernames, event names and descriptions. As in previous reports the information can be exported to a spreadsheet (Google Sheets or CSV file).
The other new addition to the Audit menu is “Mobile Devices”, however this is unlikely to be used in forensic analysis, as attackers stay away from mobile clients – as they give out too much information. For this to work, Mobile Management needs to be enabled on GSuite on the Setup Wizard:
Once this is done, Mobile Events will be available for review. As most Audit reports the data can be exported to a spreadsheet.
GSuite Enterprise does not add further “basic” forensic information, but the added feature set aims to improve security with active measures (https://support.google.com/a/answer/7284269):
- Data Loss Prevention in Google Drive: scanning content on Google Drive files and generate alerts
- Data Loss Prevention in Email: Also scanning content on email and trigger responses (quarantine, reject or censor a message)
- Automatic OCR (optical character recognition) on images to extract text – and add to the DLP measures above
- Third party email archiving
- BigQuery log retention, which can be configure to keep logs indefinitely. (https://support.google.com/a/answer/7233312)
- Hosted email encryption and advanced mobile device management rules.
The only area relevant for forensics would be the enhanced interval of log retention using BigQuery, which will take the archive beyond the stated 30 day email log retention on Basic and Business.
In Summary:
- GSuite Basic – likely the most common offering used by companies in Vietnam – has a lot of forensic information available, but has limited log retention and no coverage on Google Drive events.
- GSuite Business is a very important upgrade for those organisations that use Google Drive as their main storage, as this is the minimum level of server that provides useful forensic information there.
- GSuite Enterprise should be used by organisations that handle confidential or sensitive information. This version adds both active measures to prevent information leaks and unlimited log retention.